It is a common practice that when asking for an information from a person, especially for legal matters and data, an Authorization Form should be completed and presented as an evidence or proof of obtaining proper permission.
As soon as it is signed, the authorized company or individual will then have access to the specified data indicated on the form. This also applies to permitting an employer to verify an employee’s Social Security information with a Security Authorization Form.
Social Security Authorization
Authorization for Social Security Administration
Security Authorization
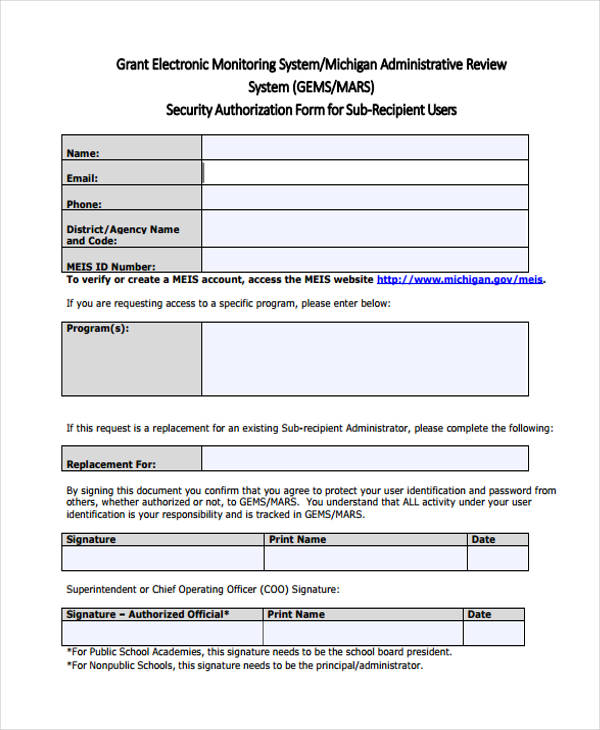
Security Authorization for Sub-Recipient User
Web Portal Security
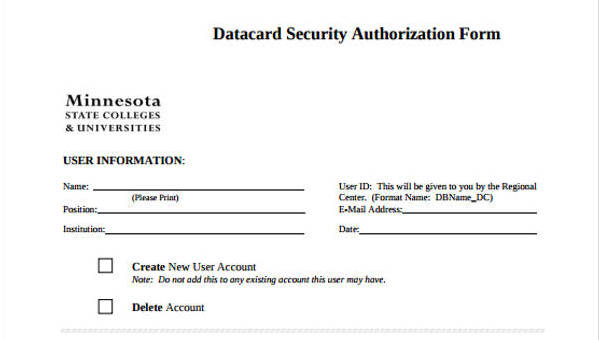
Datacard Security Authorization
What is a Security Authorization Form?
A Security Authorization Form is the document that allows an authorized person to access the security information and data of an organization or another individual. This includes the records for the security system of a company, the Social Security information of an insurance beneficiary, and even viewing the security control policy of an agency. It is important that this form is processed and submitted to the appropriate security personnel to assure that the requestor will not cause any damage with the information.
How to Complete a Security Authorization Form
Step 1: Read the instructions and understand the areas which need to be filled out.
Step 2: Fill in your personal data and the name of the person whom you will give your permission to.
Step 3: Indicate the address you want the authorized information to be sent after the process period.
Step 4: State your reasons as to why you need the information.
Step 5: Specify what sorts of data and information are to be released.
Step 6: Sign and date the form.
When dealing with transacting a deposit to the bank on someone else’s behalf, it is not a Security Authorization Form that you will need but a Direct Deposit Authorization Form. This is to indicate the amount you wish to be deposited by the authorized person on a specific date.
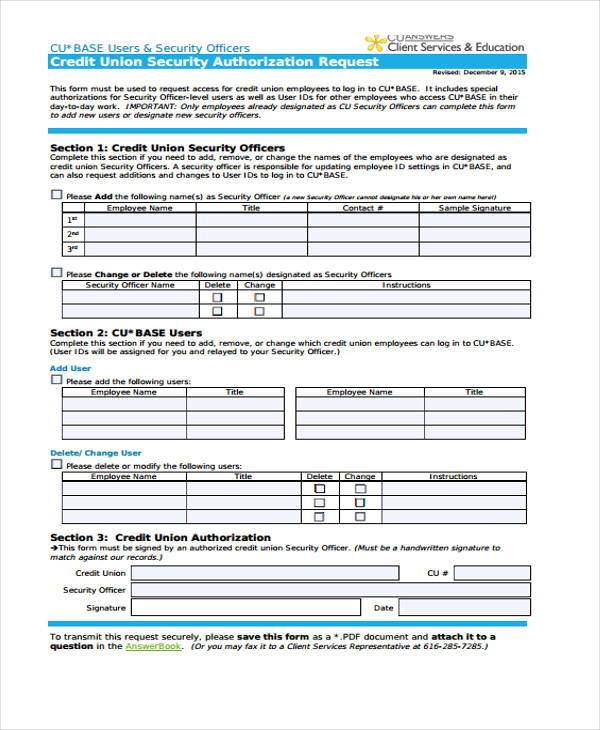
Credit Union Security Authorization Request
User Security Authorization Request
Security Snobs Authorization
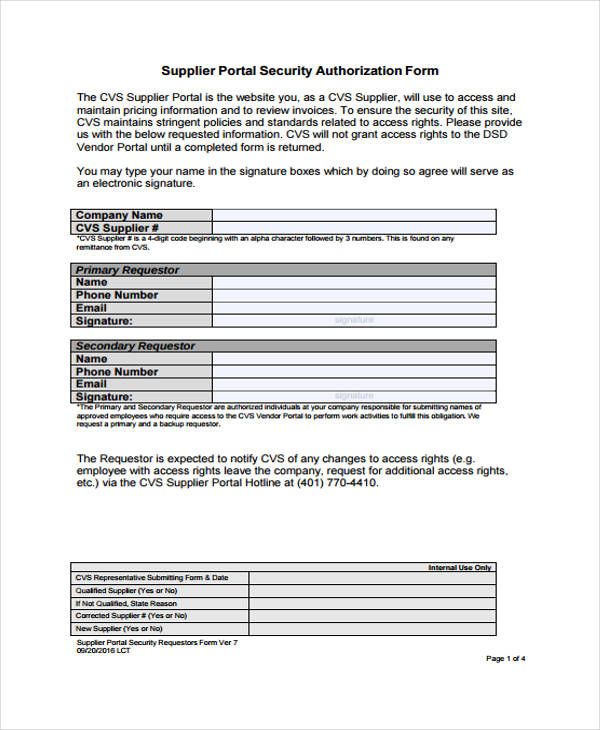
Supplier Portal Security
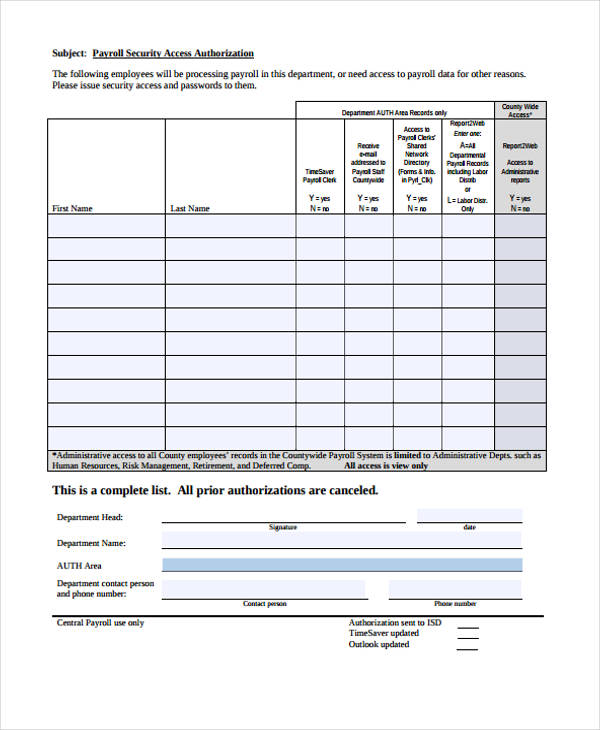
Payroll Security Access Authorization
Security/Damage Deposit Authorization
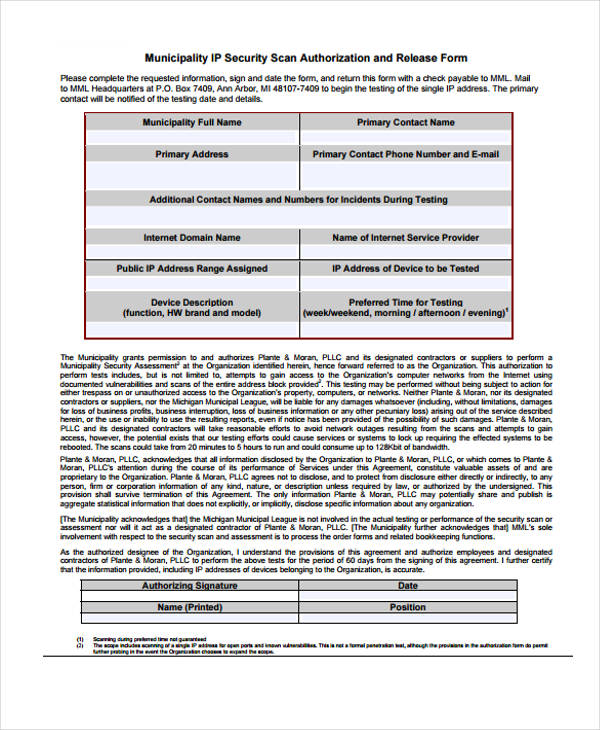
Municipality IP Security Scan Authorization
Why Use a Security Authorization Form?
There are four main reasons why an individual is required to fill out a Security Authorization Form.
The first is to allow another entity or a third party to access only the information stated on the form.
Second, to account the authorized individual for further damage of the owner’s information which will happen within the authorized time period.
Third, to comply with the rules, regulation, and laws of the government in granting access to private and confidential information.
Lastly, to audit and document the transaction done by the authorized personnel.
There are various types of forms which can give an individual the power to be authorized in doing a transaction, moving materials, and using information. When it comes to minors and children, authorization forms play a great role for the parents in assuring that their child is safe in the guidance of whoever the authorized person is. This case relates to traveling and educational trips.
The parent may approve or reject a Travel Authorization Form for their child. This document will contain the details about the travel location, time of departure, and the amount needed for the travel.
Related Posts
-
Overtime Authorization Form
-
FREE 11+ Bank Authorization Forms in PDF | MS Word
-
FREE 5+ Daycare Authorization Forms in PDF
-
FREE 10+ Paycheck Pickup Authorization Forms in PDF
-
FREE 10+ Compensatory Time Authorization Forms in PDF | MS Word
-
FREE 14+ Release Authorization Forms in PDF | MS Word | Excel
-
FREE 13+ Prior Authorization Forms in PDF | MS Word
-
Vehicle Authorization Form
-
FREE 8+ Sample Third Party Authorization Forms in PDF | MS Word
-
FREE 13+ Check Authorization Forms in PDF | MS Word
-
FREE 10+ Leave Authorization Forms in PDF | MS Word
-
FREE 9+ Sample Pre Authorization Forms in PDF | Excel
-
FREE 7+ Sample Parental Authorization Forms in PDF | MS Word
-
FREE 9+ Sample Authorization Release Forms in PDF | MS Word
-
FREE 9+ Sample Authorization Request Forms in PDF | MS Word | Excel